- New
Professional Certification Program in Cybersecurity
- 4.4/5 (1000+ Student's Ratings)
In Collaboration with

In collaboration with IBM and Microsoft, our Professional Certification Program in Cybersecurity offers cutting-edge knowledge and hands-on experience, preparing students for successful careers in these dynamic fields.
Next Cohort
This Week
Duration
09 Months . Online
360 °
Placement Assistance
Eligibility
Freshers, Graduates, Experienced
What Our Program Offers?
Our Data Science program equips you with industry-ready skills through advanced tools and expert support.
- 1:1 Doubt Clearing Session
- Live Hackathons
- Lifetime Career Support
- Webinars And Workshops
- Extensive Course Materials
- 300+ Hours of Self Paced Learning
- 400+ Hours of Live classes
- Industry Expert Mentors
- 360° Placement Assistance
- 24/7 Student Support
- Personalized Learning Paths
- Regular Assessments
- Progress Tracking
- Networking Opportunities
- Flexible Learning Schedules
- Strong Alumni Network
- Interview Preparation
- Certification Programs
- Interactive Learning Platform
- Real World Projects
What Sets inGrade Apart?

Industry-Leading Curriculum
Stay ahead with cutting-edge content designed to meet the demands of the tech world.
Expert Instructors
Learn from top professionals who bring real-world experience to every lesson.

Hands-on learning
Master skills with immersive, practical projects that build confidence and competence.

Placement-Oriented Sessions
Jump-start your career with results-oriented sessions guaranteed to get you the best jobs
Flexible Learning Options
Learn on your schedule with flexible, personalized learning paths.

Lifetime Access to Resources
You get unlimited access to a rich library of materials even after completing your course.
Community and Networking
Connect to a global community of learners and industry leaders for continued support and networking.

High-Quality Projects
Build a portfolio of impactful projects that showcase your skills to employers.

Freelance Work Training
Gain the skills and knowledge needed to succeed as freelancers.
Course Curriculum
This Cybersecurity program is designed to prepare and equip you with the main skill sets in confronting a threat from the cyber world. Some of the main subjects to be addressed are going to include network security, cryptography, and ethical hacking. The course will also take you through penetration testing, incident response, and forensic analysis so that you get hands-on experience in tackling security challenges.
- Modules
Module 01
- Introduction to Linux Fundamentals for Ethical Hacking
- Linux basics and its significance in ethical hacking
- Linux distributions and their suitability for ethical hacking
- Setting up a virtual lab environment
Module 02
- Linux System Administration
- Installation and configuration of a Linux distribution
- Basic Linux commands for system administration
- User and group management
- File system permissions and access control
Module 03
- Linux Command-Line Interface
- Introduction to the Linux shell
- Navigating the file system
- Working with files and directories
- Input/output redirection and piping
Module 04
- What is Ethical Hacking?
- Types of Hackers
- Who is a Hacker?
- Security Challenges Scanning
- Skills required for an Ethical Hacker
- Types of Attacks
- What do Ethical Hackers Do?
- Vulnerability Research
- Effects of Hacking
- How can Hacking be Ethical?
- Types of Data Stolen from the Organization
- What a hacker Do using Google Hacking
- Footprinting using Google Hacking Technique
- Google Advance Search Operators
- What is Penetration Testing?
Module 05
- Introduction to Security Operations Center (SOC)
- SOC Roles and Responsibilities
- SOC Tools and Technologies
- Threat Intelligence and Information Sharing
- Incident Detection and Response
- Security Incident Handling and Management
- Log Management and Analysis
- Security Monitoring and Alerting
- Security Incident Investigation
- Vulnerability Management
- Security Incident Reporting and Communication
- SOC Metrics and Key Performance Indicators (KPIs)
- Automation and Orchestration in SOC
- Compliance and Regulatory Requirements in SOC
- STEM tools
- Case Studies and Real-world Examples
Module 06
- Tools and Methods Used in Cybercrime
- Proxy Servers and Anonymizers
- Phishing
- Password Cracking
- Key loggers and Spywares
Module 07
- Password Complexity
- Password Cracking Techniques
- Types of Password Attacks
- Microsoft Authentication
- How Hash Passwords are Stored in Windows SAM?
- PWdump7 and Fgdump
- Laze Soft
- Ophcrack
- Cain & Abel
- Detail Study on Password Cracking Tools
- Key logger
- Types of Keystroke Loggers
- Detail Study on Key loggers and Spy ores
Module 08
- Steganography Techniques
- How Steganography Works
- Types of Steganography
- Methods of Steganography
- Steganography Detection Tools
- Cryptography
- Types of Cryptography
- Cryptography Techniques
- What is SSH
Module 09
- What is Social Engineering
- Behaviors Vulnerable to attacks
- Why is Social Engineering Effective
- Warning Signs of an Attack
- Phases in a Social Engineering attack
- Impact on the Organization
- Command Injection Attacks
- Common Targets of Social Engineering
- Types of Social Engineering
- Social Engineering Through Impersonation On Social
- networking Sites
- Risks of Social Networking to Corporate Networks
- Social Engineering Countermeasures
Module 10
- Network architecture
- Protocols and technologies
- Layered architecture, open systems interconnect
- (051) model
- Transmission control protocol
- Internet protocol (TCP/IP)
- Hybrid, TCP/IP model
- Application layer protocols: HTTP, SNMP, DNS, POP,
- SMTP
- Transport layer protocols: transmission control protocol
- (TCP), user datagram protocol (UDP)
- Network/ Internet layer protocols Internet protocol
- (IP)v4, IPve, IPsec protocols
- Link layer protocols: Address Resolution Protocol (ARP)/ Reverse ARP/ Proxy ARP, Ethernet, VLAN
Module 11
- Cloud computing architectural framework
- Concerns and best practices
- Governance and enterprise risk management
- Legal issues: contracts and electronic discovery
- Compliance and audit management
- Information management and data security
- Interoperability and portability
- Traditional security, business continuity, and disaster recovery
- Data center operations Incident response
- Application Security
- Encryption and key management
- Identity, entitlement, and access management Virtualization and Security as a service
Module 12
- What is CDR?
- CDR Investigation
- CDR Report Preparation
Module 13
- Computer Forensics Fundamentals
- Computer Forensics Investigation Process
- Understanding Hard Disks and File Systems
- Data Acquisition and Duplication
- Defeating Anti-forensics Techniques
- Windows Forensics
- Network Forensics
- Investigating Web Attacks
- Dark Web Forensics
- Investigating Email Crimes
- Malware Forensics
Module 14
- Basics of forensic science
- Fingerprints and document analysis
- Handwriting analysis
- Criminology and crime scene investigation
- Ballistics
- Soft Skills Program
- Resume Building
- Communication Skills
- Interview Preparation
- Time Management
- HR Round Guidance
- E-mail Writing
- Personality Development
- Emotional Intelligence
- Conflict Management
- Salary Negotiation
- Creativity
- Get Certification

Professional Certification Programin Cybersecurity
09 Months . Online-
100% Secure Transactions
-
Multiple Payment Options
-
24/7 Payment Support
-
EMI Option Available
Languages and Tools Covered










































Projects
Network Vulnerability Assessment
Provides a clear picture of the organization’s security posture by identifying existing vulnerabilities and misconfigurations. Helps prioritize security measures and allocate resources effectively, reducing the risk of potential attacks.
Skills Needed →
Phishing Simulation
Tests and enhances employee awareness of phishing attacks through practical experience. Reduces the likelihood of successful phishing attempts, protecting sensitive information and organizational integrity.
Skills Needed →
Incident Response Plan Development
Establishes a structured approach for responding to cybersecurity incidents, ensuring swift and efficient action. Minimizes damage during an incident, reduces recovery time, and enhances overall organizational resilience against attacks.
Skills Needed →
Penetration Testing
Identifies security weaknesses before they can be exploited by malicious actors through controlled, ethical hacking. Strengthens application and network security, safeguarding sensitive data and maintaining customer trust.
Skills Needed →
Malware Analysis
Provides insights into the behavior and characteristics of malware, enhancing the ability to detect and respond to future threats. Informs the development of effective defense strategies and threat mitigation techniques.
Skills Needed →
Secure Web Application Development
Embeds security best practices into the software development lifecycle, creating applications that are less susceptible to attacks. Increases user trust, protects sensitive data, and ensures compliance with security regulations.
Skills Needed →
Cybersecurity Awareness Training Program
Educates employees about cybersecurity threats and best practices, fostering a security-aware culture within the organization. Reduces the likelihood of human error, which is often a significant factor in security breaches.
Skills Needed →
Data Loss Prevention Strategy
Implements measures to protect sensitive data from unauthorized access and breaches, enhancing compliance with regulations. Safeguards organizational assets, maintains customer trust, and mitigates the financial impact of data breaches.
Skills Needed →
Case Studies
Hiring Partners







































































Meet our inGraders





























Application Process for inGrade

Career Consultation
Assess eligibility with our Career Counsellor.

Personalized Guidance
Receive an acceptance letter if eligible.

Easy Registration
Pay the booking amount to confirm your seat.

Start Upskilling
Access the curriculum and begin your journey.

Ongoing Support
Receive continuous mentorship and career assistance.

Live Interactive Sessions
Join instructor-led live sessions where you can ask questions, join discussions, and engage with peers. The live sessions will help deepen your understanding while keeping you connected throughout the program.
Live Interactive Sessions
Join instructor-led live sessions where you can ask questions, join discussions, and engage with peers. The live sessions will help deepen your understanding while keeping you connected throughout the program.

Self-Paced Learning Content
Start your learning journey with our comprehensive self-paced modules. Access video lessons, reading materials, and exercises that fit your schedule, allowing you to learn at your own pace and revisit topics whenever needed.


Regular Evaluations
Track your progress with regular assessments. Through quizzes, assignments, and hands-on projects, you’ll continually measure your understanding and improve your skills, ensuring you stay on course.
Regular Evaluations
Track your progress with regular assessments. Through quizzes, assignments, and hands-on projects, you’ll continually measure your understanding and improve your skills, ensuring you stay on course.

Personalized Doubt Sessions
If you need extra help, our experts are available for personalized, one-on-one doubt clearing sessions. Get the support you need to tackle challenging topics at any time confidently.


Hands-On Projects & Case Studies
Work on practical, real-world projects and case studies simulating real-world industry challenges. You apply what you have learned by hands-on approach while enhancing your ability to think critically and creating a portfolio you can take to employers.
Hands-On Projects & Case Studies
Work on practical, real-world projects and case studies simulating real-world industry challenges. You apply what you have learned by hands-on approach while enhancing your ability to think critically and creating a portfolio you can take to employers.

Focused Learning Tracks
Choose specific learning tracks, which focus on specialized learning tracks, including machine learning, data visualization, or artificial intelligence, focusing on what really interests you most and where it would take you towards achieving your career goals.


Industry-Specific Expertise
Get in-depth knowledge in your desired field, whether it’s healthcare, finance, or e-commerce. This specialized expertise will help you stand out and make you more competitive in your industry of interest.
Industry-Specific Expertise
Get in-depth knowledge in your desired field, whether it’s healthcare, finance, or e-commerce. This specialized expertise will help you stand out and make you more competitive in your industry of interest.

Interview Preparation
Be prepared to succeed with comprehensive interview coaching that covers technical, behavioral, and case study questions. Our support extends to career counseling, including resume reviews, job search strategies, mock interviews, LinkedIn optimization, and much more.

Alumni Highlights
-
350+
Global Companies Hiring -
7 LPA
Average CTC -
40 LPA
Highest CTC -
85%
Average Salary Hike
Learning is better with Ingrade
- Launch your career in Cyber Security today
- Earn up to ₹ 40 LPA at leading companies
- For college students, graduates & working professionals
👋 Connect with our Experts for Counselling Session
Frequently Asked Questions
What is the duration of the Cybersecurity program?
The program duration is 9 months and covers a wide range of cybersecurity topics, including network security, cryptography, and ethical hacking.
Do I need some prior technical knowledge to join this Cybersecurity program?
No, the program is designed both for beginners and people with experience. Even the most basic topics-cybersecurity basics and network security will be a great foundation to your building from the word go.
What support will I receive during the program?
You will have access to a dedicated support team, mentorship from industry experts, and live Q&A sessions to help you with both course content and career guidance.
Will I have access to the course materials after completing the program?
Yes, you will have lifetime access to all course materials, recorded sessions, and the Learning Management System (LMS) for continued learning.
Are there live doubt-clearing sessions in this program?
Yes, we offer live online sessions for clearing doubts, along with 24/7 interaction with trainers to support your learning journey.
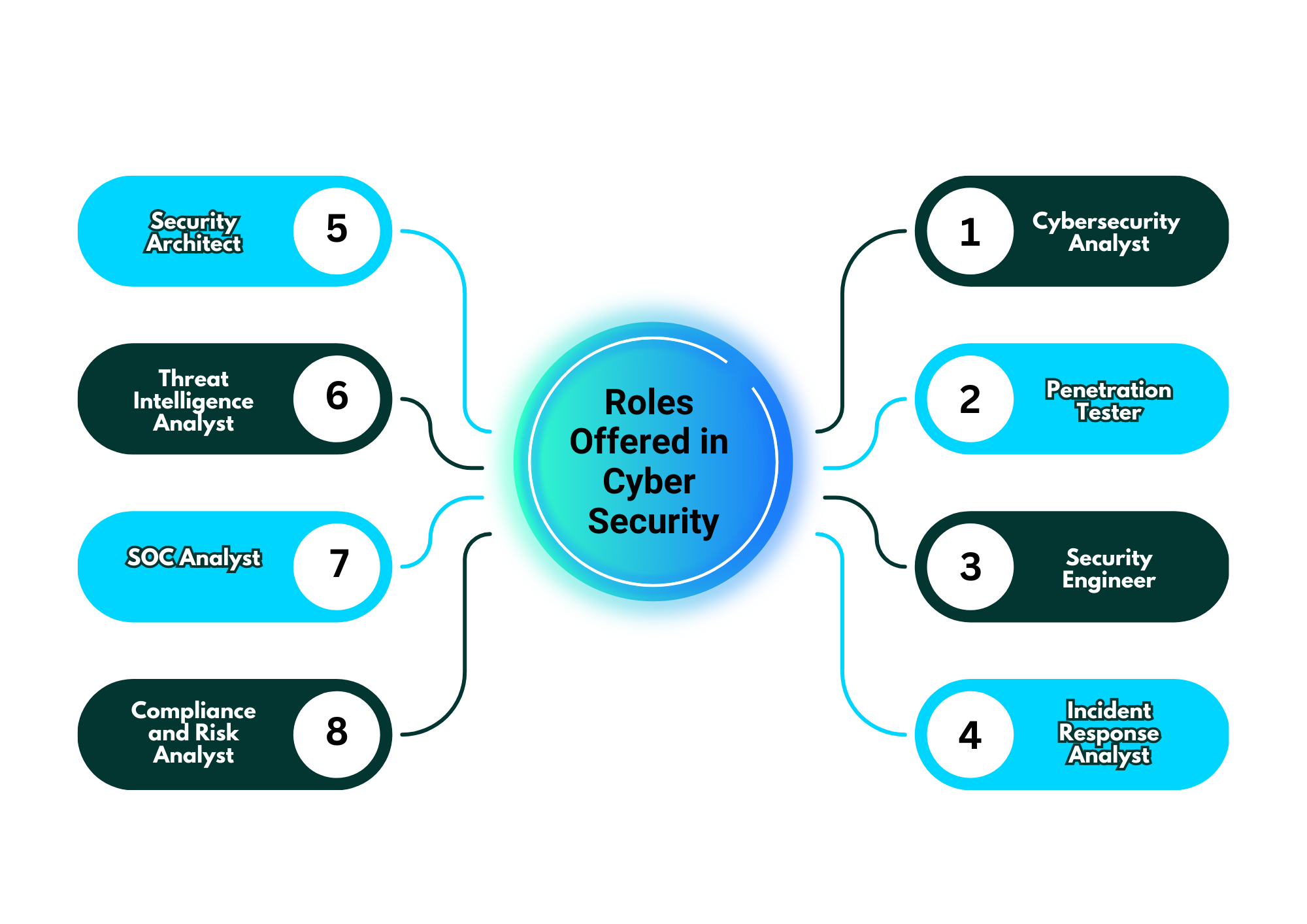
What career roles can I apply for after completing the program?
What career roles can I apply for after completing the program?
Will I get assistance with job placement after the program?
Yes, the program includes career services such as mock interviews, resume building, and placement support to help you secure a cybersecurity job.
What type of hands-on project work is incorporated into this program?
Your practical learning will be enhanced through hands-on project work which includes penetration testing, securing a wireless network, simulating cyber-attacks, and many more.
Does this program include ethical hacking?
Yes, ethical hacking and penetration testing are a part of the course wherein you get to explore the usage of hacking tools like Metasploit and methodologies used by security professionals.
What practical skills will I gain from the program?
You will develop skills in threat detection, risk assessment, incident response, securing networks, and ethical hacking, using industry-standard tools and frameworks.



